The Art Of Information Hiding ( Steganography ) - Lab 4
Published on December 20, 2023.
The art of information hiding involves concealing data within a carrier, ensuring its confidentiality and integrity. It encompasses various techniques aimed at securing information from unauthorized access or detection. Steganography and cryptography are the primary methods used in this domain.
Understanding Steganography
Steganography, a practice dating back to ancient times, is the art of concealing messages within other non-secret data or media. Unlike cryptography, which focuses on making messages unreadable to unauthorized parties, steganography hides the existence of the message itself. The primary goal is to ensure the secrecy of communication rather than its security through encryption.
This technique can be applied to various mediums such as images, audio files, text, and even video. In digital steganography, information is subtly embedded into the carrier file without noticeably altering its appearance or quality. For instance, changing the least significant bits of pixel values in an image or manipulating whitespace in text files are common methods.
Steganographic methods range from simple, like hiding messages within the whitespace of a text document, to complex, involving advanced algorithms to embed data in the frequency domain of multimedia files. Some popular steganographic techniques include LSB (Least Significant Bit) insertion, hiding text within image metadata, or even using specific fonts or styles to hide messages in plain sight.
Using Steganography
Over the next steps, I will embed a secret plaintext file within a .txt format into image and audio files. The demos will use the winhip_en.exe software for hiding files.
Step 1: Preparing The plain text file.
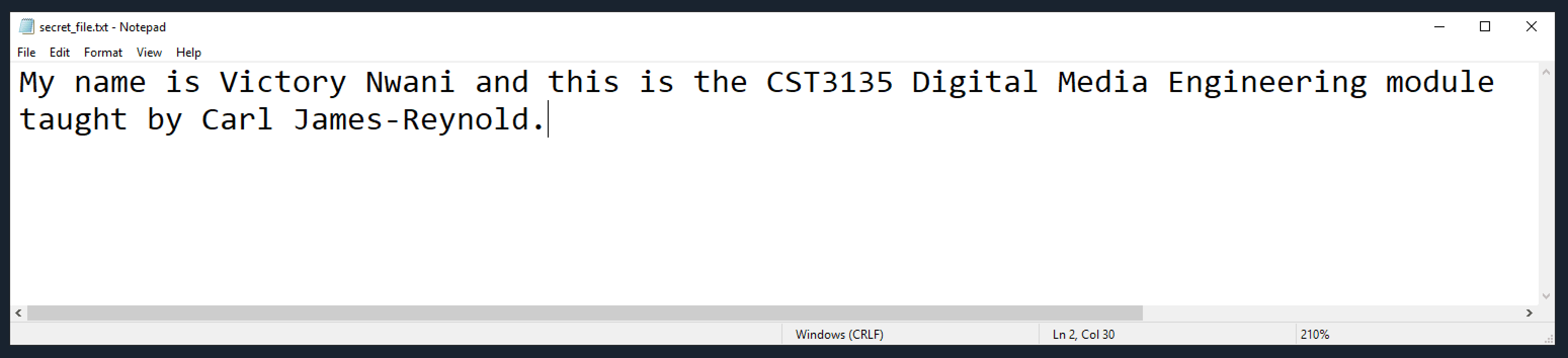
The plaintext file for this demo contains the following sentence: my name, the name of this course module, and its professor.
"My name is Victory Nwani and this is the CST3135 Digital Media Engineering module taught by Carl James-Reynold."
Step 2: Opening the carrier image
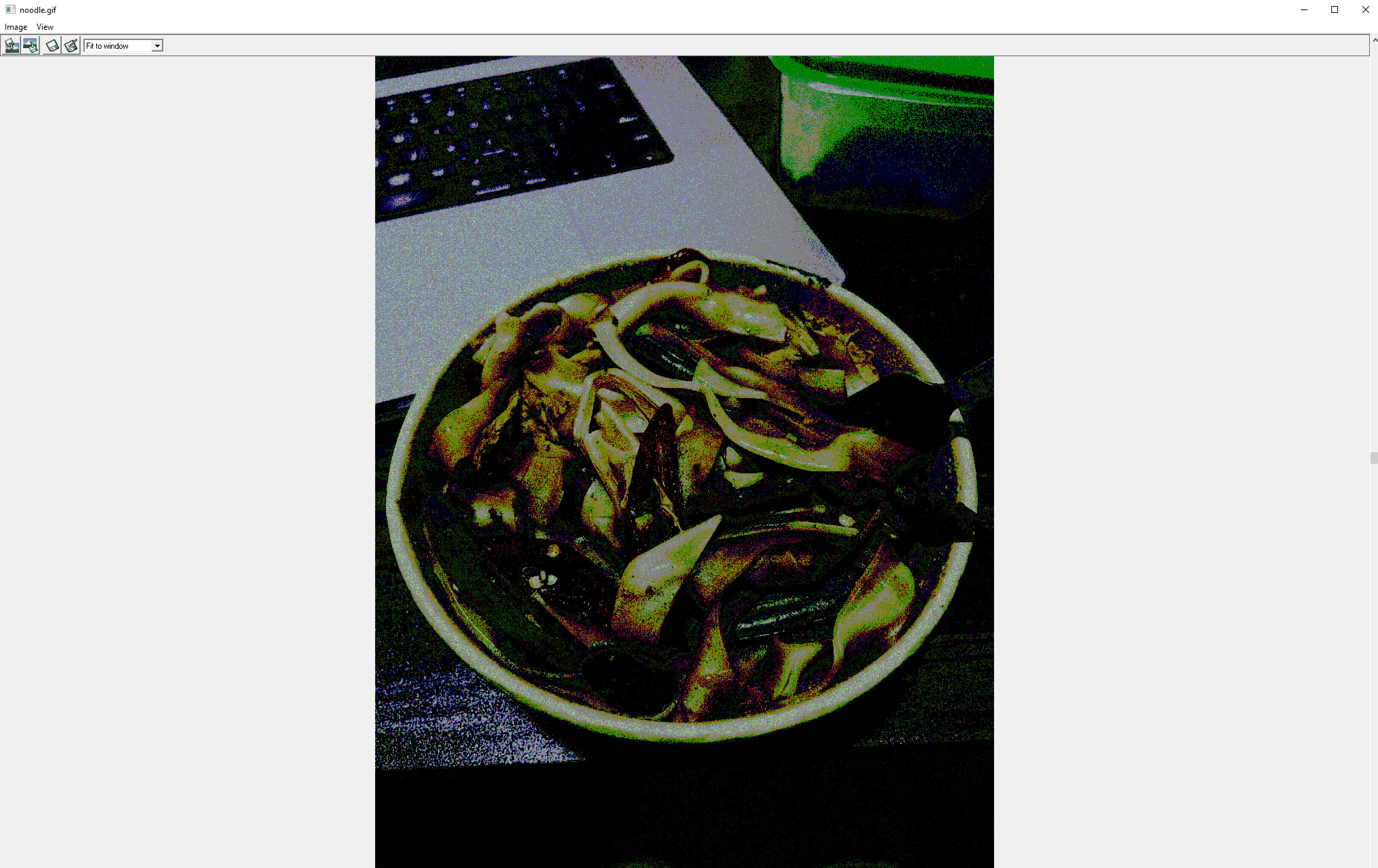
My carrier image for this demo shows a drunken noodles meal I was gifted by a friend from an Asian restaurant 😍. The word "carrier" is used because the image carries an embed within it.
When opened with the winhip_en software, it gives the following look which shows a much-increased image noise due to the embedding.
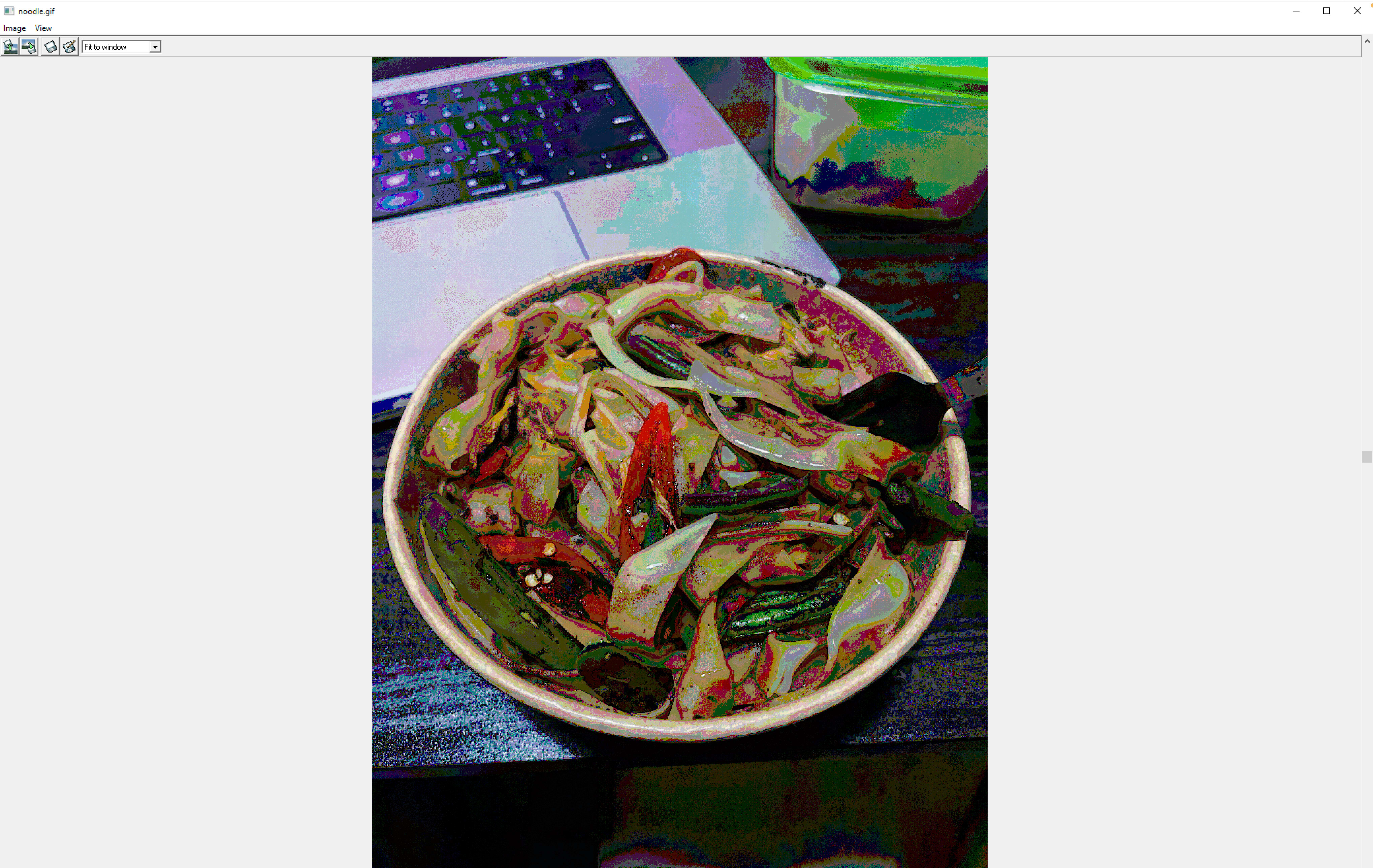
I took the image above with my iPhone 12 and it was produced in a HEIC format by iOS. The image was converted using PhotoShop into a .gif format for the winhip_en software.
NOTE: The winhip_en software supports images in .bmp and .gif formats.
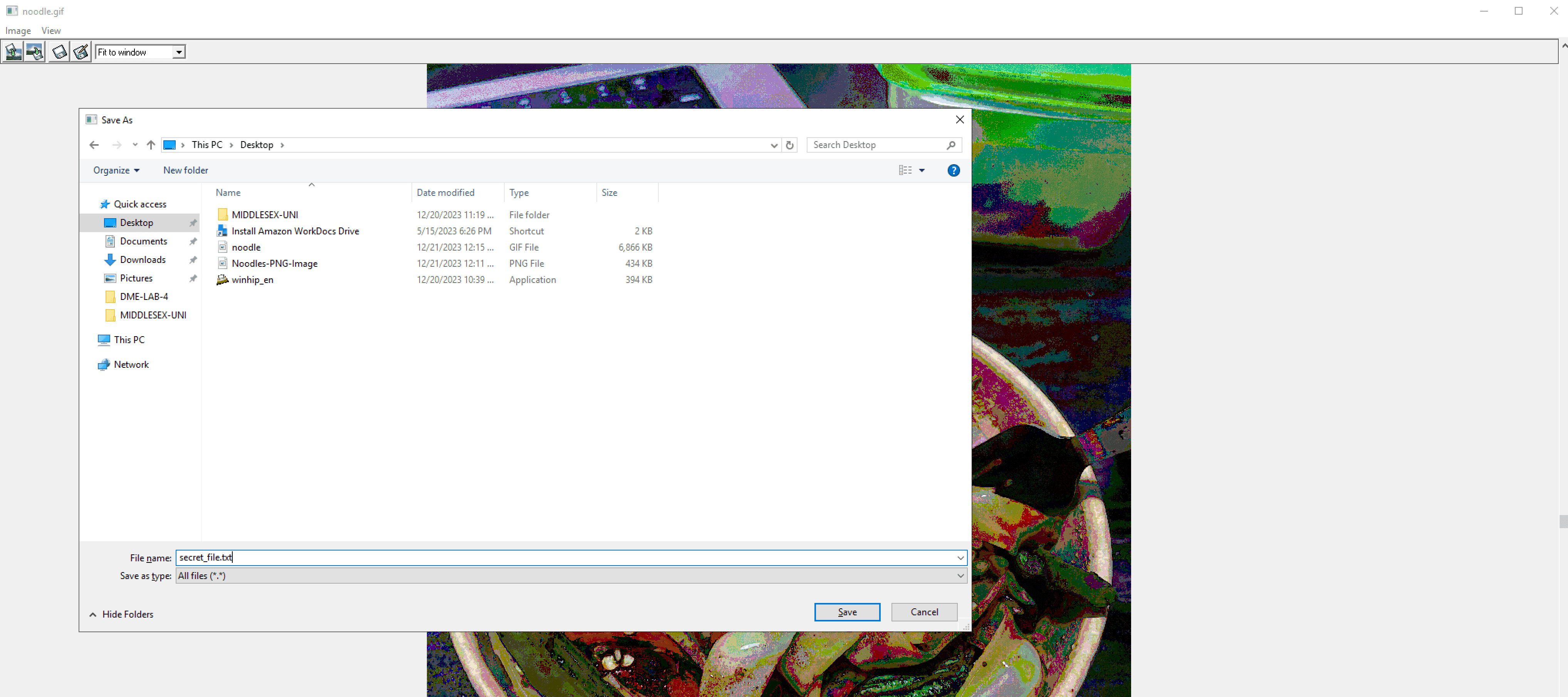
Step 3: Embedding the secret file
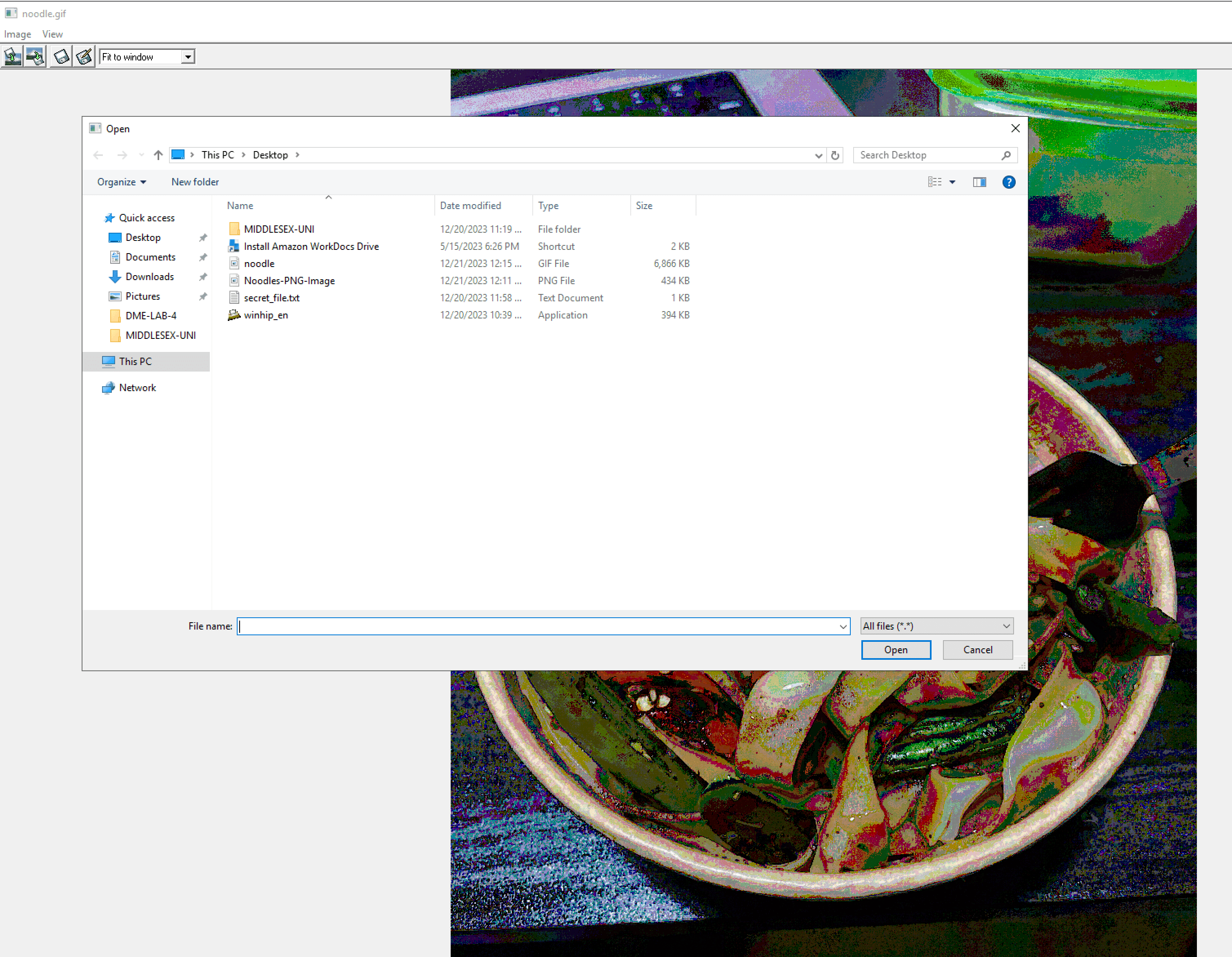
Clicking the top-right Embed icon enables me to launch the Windows file explorer to select a secret file that I want to embed.
From the file explorer, I have to select the secret file I want to embed into the image:
Winhip_en will prompt me to specify a password after selecting my secret file. It also presents a dropdown to select either the Blowfish or Rjindael algorithms.

Step 4: Retrieving the secret file
At this point, I have embedded a secret plaintext file into my drunken noodles image. I can now share the files with my friends without them knowing I have hidden a file within the image. I can also use this as a way to hide information for only me to view on a shared computer.
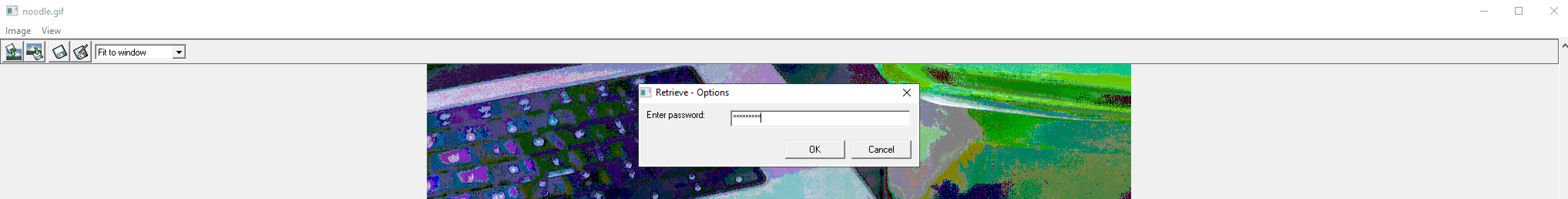
To view the hidden file, I need to click the top-right retrieve file button.
Winhip_en will prompt me to enter the password specified for the file.
Winhip_en will launch the Windows File Explorer prompting me to save the retrieved file.
Lab Evaluations
These were the following questions used to evaluate my participation in this lab.
Question 1: What happens if you embed a large file?
I attempted to hide a large file of another image with a 6.8MB size into the drunken_noodles image.
I observed the following:
The hiding progress dialog took far much amount of time to complete.
The pixels within the image had darker shades after embedding the large image.
The image below shows the original image look before embedding the large image:

The next image shows the original image look after embedding the large image:
Question 2: Does the file size change when you add a message?
Yes, the file size was slightly increased after embedding an 6.8MB image. The file size of the drunken_noodles image was modified from 6.886KB to 6.887KB after the embedd.
The image below shows the original image size before embedding the large image:

The image below shows the original image size after embedding the large image:

Question 3: What are the implications of this type of technology?
Steganography has over its years of existence proven to have various negative and positive implications on the digital industry.
Some pros of Steganography include:
The communication of sensitive data without arousing the interest of third parties.
The concealment of data when being transmitted.
Some of the cons of Steganography include:
The violation of legal and ethical policies when transmitting files having embeds to unsuspecting individuals.
There is a high chance of corrupting the carrier file while embedding another file.
Conclusion
Within this lab, I learned about the history of information hiding down from the Greeks and how it has morphed into Steganography in our modern times.
Further Readings
An Overview of Image Steganograpy by T. Morkel 1, J.H.P. Eloff 2, M.S. Olivier 3.
Exploring steganography: Seeing the unseen by Neil F. Johnson Sushil Jajodia.
The history of steganography by David Khan.